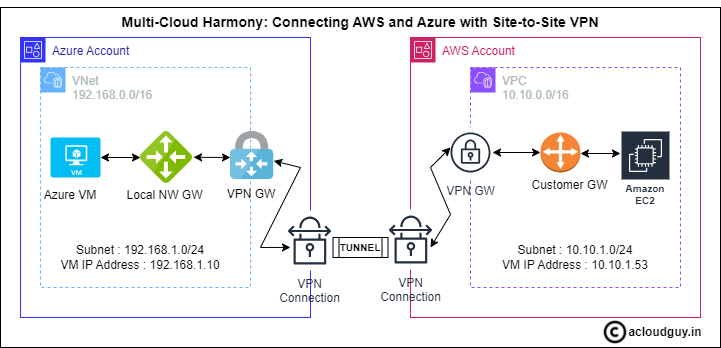
Multi-Cloud Harmony: Connecting AWS and Azure with Site-to-Site VPN
In the evolving landscape of cloud computing, the adoption of multicloud architectures has become a common strategy for businesses aiming to address diverse operational needs. This approach involves distributing data and resources across multiple cloud providers, with AWS, Azure and GCP standing out as the most prevalent choices. As a solution architect, mastering the management of the entire multicloud perimeter is crucial. One fundamental aspect is establishing connections between cloud environments to enable seamless communication across resources.
This blog focuses on bridging AWS and Azure through the implementation of a Virtual Private Network (VPN). By doing so, you can create a unified cloud environment, promoting collaboration and resource sharing. To enhance resilience, security and ensure private connectivity, the setup will involve the creation of a VPN tunnel.
For Seamless Secure Private Cross-Cloud Integration
1. Hybrid Cloud Deployments:
- Use Case: Organizations may have existing infrastructure on both AWS and Azure due to historical reasons, mergers, or specific service preferences.
- Benefits: Linking the two environments allows for a cohesive hybrid cloud strategy, enabling seamless data and workload movement between the on-premises, Azure, and AWS environments.
2. Multi-Cloud Disaster Recovery:
- Use Case: Ensuring business continuity is crucial, and some enterprises choose to leverage both Azure and AWS for disaster recovery purposes.
- Benefits: Establishing VPN connections enables the replication of critical data and applications across clouds, providing redundancy and quick recovery in case of a failure in one cloud provider.
3. Vendor Diversification and Risk Mitigation:
- Use Case: Companies seeking to mitigate vendor lock-in risks or wanting to take advantage of specific services from each provider.
- Benefits: By linking AWS and Azure, businesses can maintain flexibility in choosing the best services from each provider while avoiding dependency on a single vendor. It also provides a fallback option in case of service outages or disruptions.
4. Compliance and Data Residency:
- Use Case: Adherence to specific data residency or compliance requirements may necessitate the use of different cloud providers for different regions.
- Benefits: Establishing VPN connections ensures that data can be securely transferred and accessed across compliant regions, helping businesses meet regulatory requirements without compromising on operational efficiency.
Prerequisite —
- AWS Account with IAM Admin privileges.
- Azure Account with Admin privileges.
AWS & AZURE Services Usage —
- AWS VPC, IAM, EC2, SG, CLOUDFORMATION, VPG, CGW, VPN
- AZURE VNET, Resource group, VPN Gateway, Local Gateway, S2S Connection, Virtual Machines.
STEP BY STEP GUIDE -
STEP 1 : Clone the GitHub Repo.
- Navigate to following GitHub Repository AWS-AZURE-S2S-VPN
- Clone the repo to download the CloudFormation Template for VPC.
- CloudFormation template name — VPC_With_Managed_NAT_And_Private_Subnet.yaml
STEP 2 : Creating AWS VPC through CloudFormation service.
- Login to AWS account, Navigate to AWS CloudFormation Service.
- Head over & change the region of the aws console where you want to deploy the resources & VPN.
- Click on Create Stack & upload the template downloaded in the step 1.
- Keep rest of the settings as default & hit create.
- It will create a New VPC along with IGW, NAT Gateway, Public & Private subnets, Route Tables, IAM roles.
- AS NAT Gateway is involved we are going to get charged for NAT Gateway as per the AWS VPC Pricing.

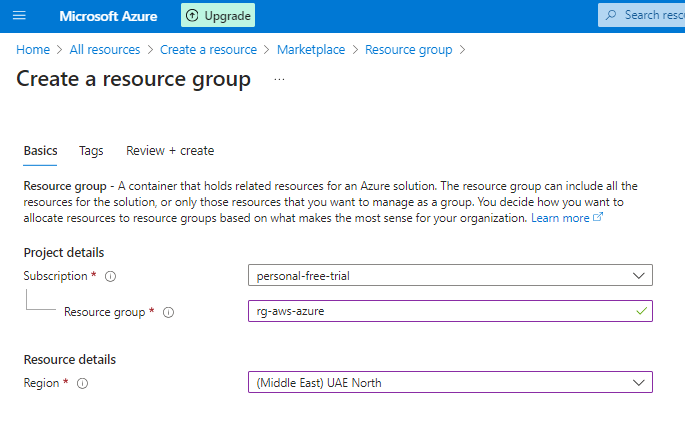
STEP 3 : Creatin Azure Vnet through Azure console.
- Login to Azure account, Navigate to Resources groups.
- Create a resource group on Azure to deploy the resources.
- Select the subscription you want to use for this activity.
- Resource Group Name: your choice
- Region: your choice
- Review + Create = Deployment complete.
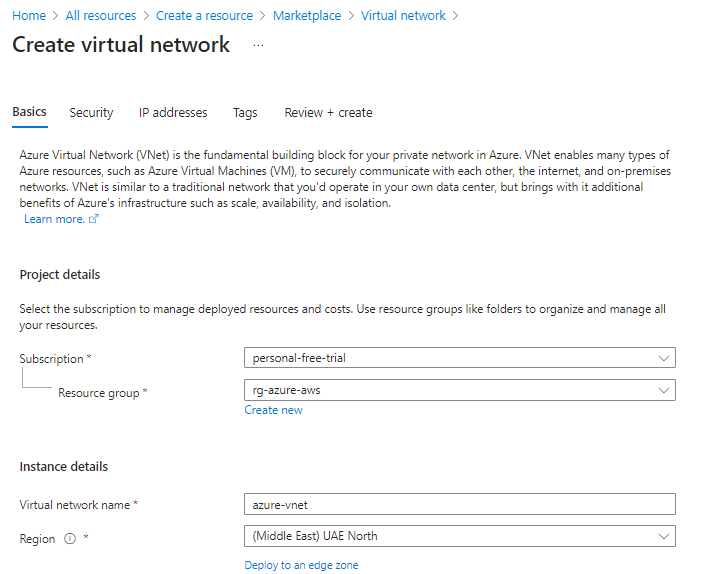
- Now head over to Create Virtual Network
- Select the Resource Group Name created above.
- Select the same Region as above.
- VNet Name: your choice
- VNet IPv4 Address Space: 192.168.0.0/16
- Subnet Name: your choice
- Subnet IPv4 Address Space: 192.168.1.0/24
- Review + Create = Deployment complete.
- IMP : Go ahead to subnets section & create a new GatewaySubnet.
- This subnet will be used by Azure VPN Gateway as depicted in architecture diagram.
STEP 4 : Creating Azure VPN Gateway through Azure console.
- Navigate to Azure VPN Gateway.
- VPN Gateway Name: your choice
- Region: your choice
- Gateway Type: VPN
- SKU: VpnGw1
- Generation: Generation 1
- Virtual Network: vnet-azure
- Public IP Address Name: pip-vpn-azure-aws
- Public IP Address Type: Standard
- Assignment: Assignment
- Enable active-active mode: Disabled
- Configure BGP: Disabled
- Review + Create = Deployment complete.
- It will take around 45–60 minutes for Azure VPN deployment to get completed & come active.

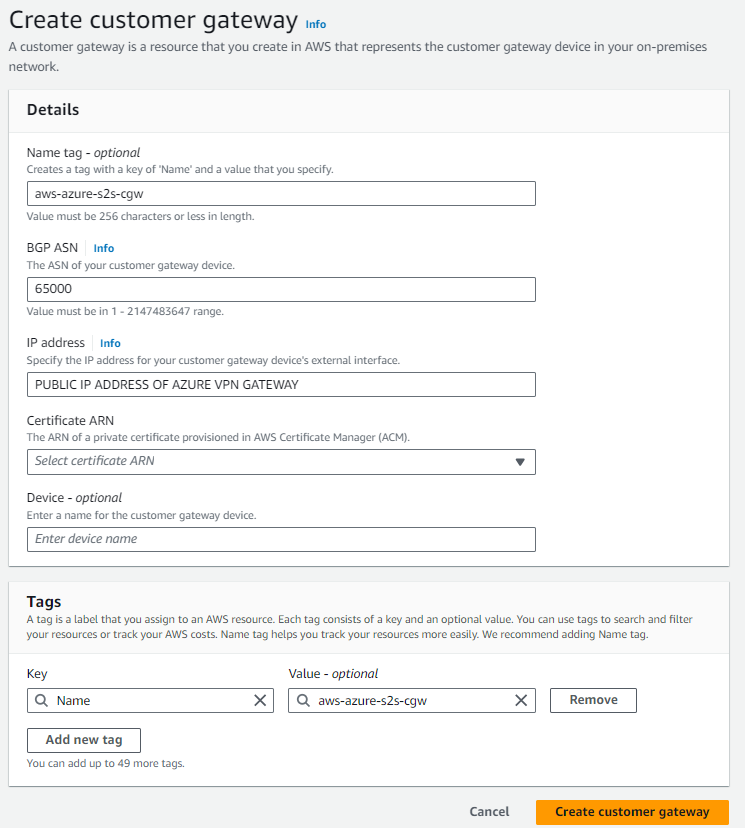
STEP 5 : Create a customer gateway pointing to the Public IP Address of Azure VPN Gateway
- Navigate to AWS VPC -> Customer Gateway.
- NAME : Enter the name for AWS Customer Gateway. <your choice>
- BGP ASN : Keep it as it is
- IP address : Enter the Public IP address of Azure VPN Gateway
- Hit Create & let it become active.
STEP 6 : Create the AWS Virtual Private Gateway then attach to the VPC
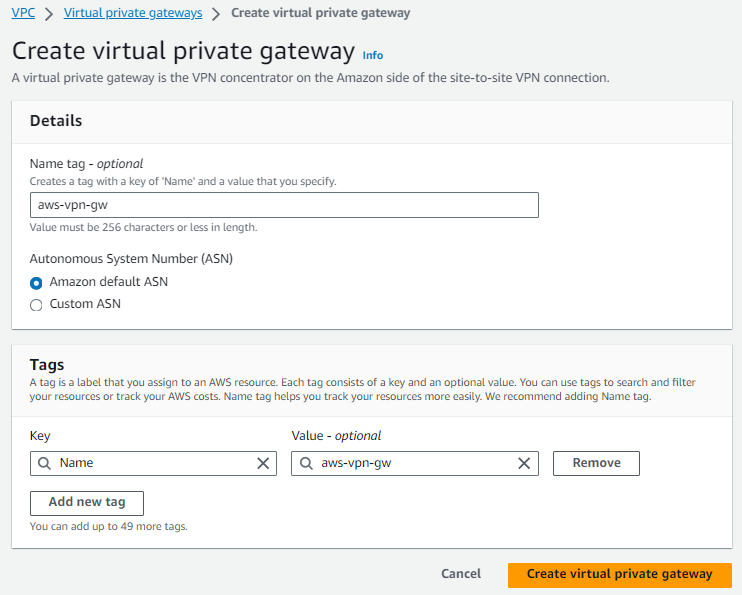
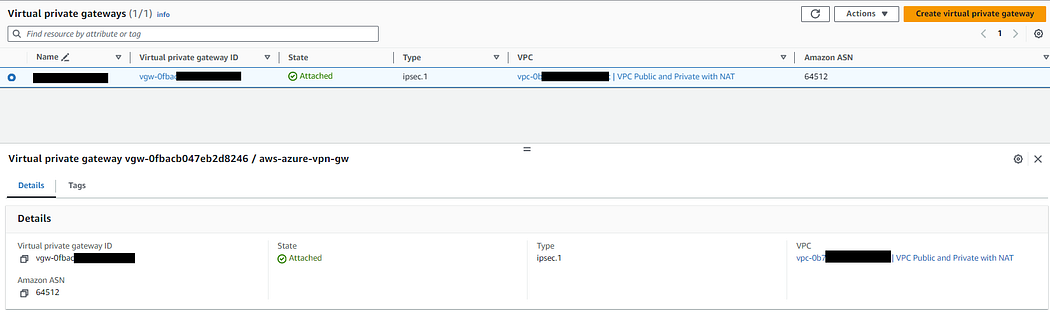
- Navigate to AWS VPC -> Virtual Private Gateway.
- Name: your choice
- Hit Create & after its status shows detached.
- Go to Actions on right hand of screen & select Attach VPC.
- Attach the VPC created in Step 1.
- Wait for its status to change to attached.
STEP 7: Create a site-to-site VPN Connection in AWS Console.
- Navigate to AWS VPC -> Site-to-Site VPN connections.
- Create a New VPN Connection.
- Name: your choice
- Target gateway type: Virtual private gateway (Select your Virtual private gateway created in step 6)
- Customer gateway: Existing (Select your Customer gateway created in step 5)
- Routing options: Static
- Static IP prefixes: 192.168.1.0/24 (Azure Subnet created in step 3)
- Leave rest of them as default
- Hit Create VPN connection.
STEP 8: Download the AWS VPN configuration file for Azure Tunnel Configuration
- Navigate to AWS VPC -> Site-to-Site VPN connections.
- Once the VPN connection is active in status.
- Click on Download Configuration & select dropdown.
- Vendor: Generic, Platform: Generic, Software: Vendor Agnostic
- In this configuration file you will note that there are the Shared Keys and the Public Ip Address for each of one of the two IPSec tunnels created by AWS. ( Highly Confidential Information )
STEP 9: Creating Azure Local Gateway.
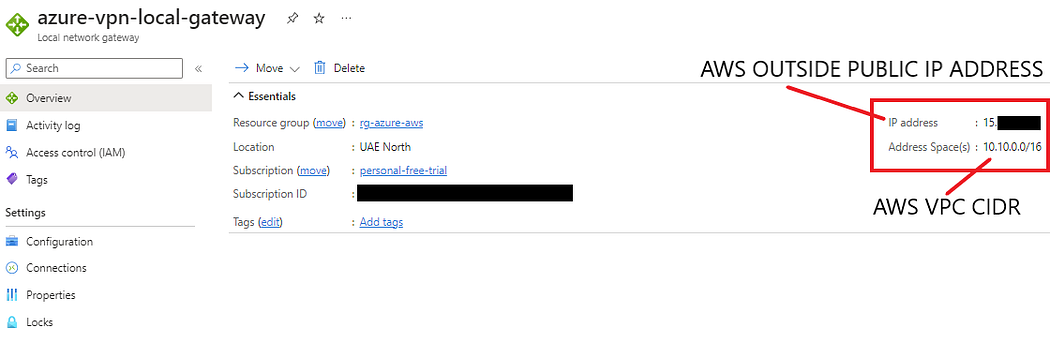
- Navigate to Azure Console -> Search Local network gateways
- Create a new Local network gateways
- Name: your choice
- Resource Group Name: created in step 3
- Region: same as previous choice
- IP address: Get the Outside IP address from the configuration file downloaded in step 8. (You can also get this info from AWS VPN Connection Section -> Tunnel Status.
- Address Space(s): 10.10.0.0/16 (AWS VPC CIDR Created in Step 2)
- Leave rest of them as default.
- Review + Create = Deployment complete.
STEP 10: Create the connection on the Virtual Network Gateway in Azure
- Navigate to Azure Console -> Search Virtual Network Gateway
- Go to connections -> Add
- Name: your choice
- Connection Type: Site-to-Site
- Local Network Gateway: Select the Local Network Gateway which you created in step 9.
- Shared Key: Get the Shared Key from the configuration file downloaded in step 8.
- Wait till the Connection Status changes to — Connected
- In the same way, check in AWS Console for the status of 1st tunnel in VPN Connection.
- Once both side shows connected, It means your phase 1 tunnel is UP.
- If not then it means you made a mistake along the way.
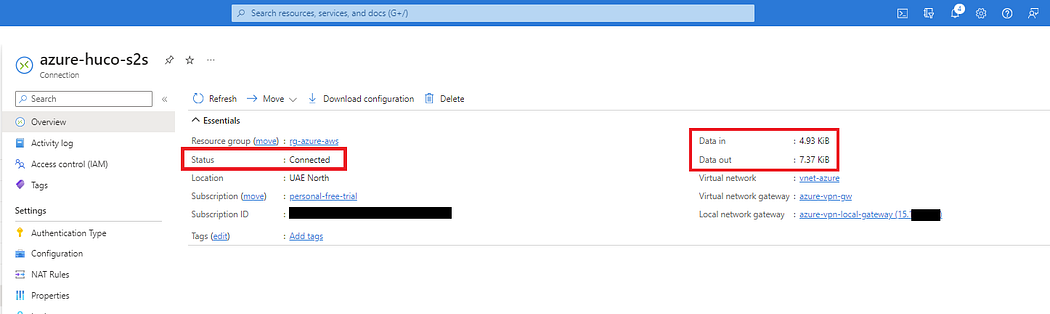
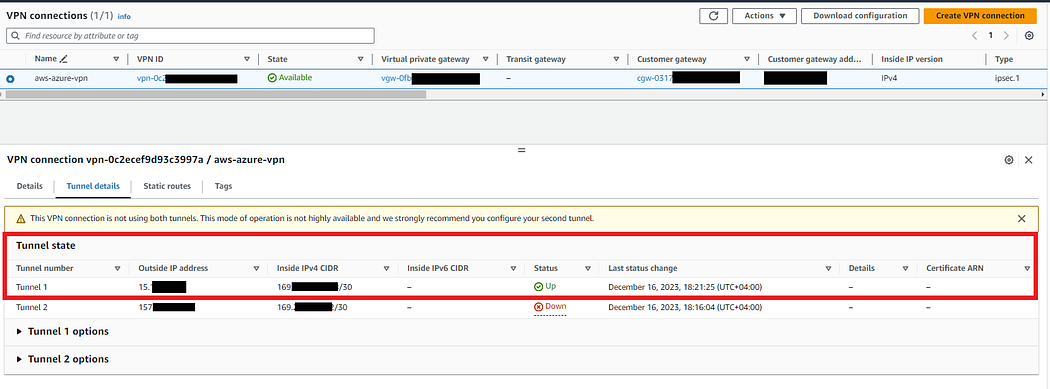
VERY IMPORTANT STEP:
STEP 11: Edit the route table associated with our AWS VPC
- Add the route for Azure subnet through the AWS Virtual Private Gateway
- Goto Public Route Table ( It will have IGW attached in routes )
- Add Destination: 192.168.1.0/24
- Target: Virtual Private Gateway that we created in step 6.

STEP 12: Create Virtual Machines in both AWS & Azure cloud.
- Create a AWS Linux/Windows VM in the same AWS VPC Network, Public Subnet with Public IP address Assignment.
- Make sure Security Group allows traffic for ICMP, SSH.
- Create a Azure Virtual Machine (Ubuntu/Windows) in the same Azure Vnet & Subnet allowing traffic for ICMP.
- Once the VM are active try ping AWS to Azure & Azure to AWS.
- This successful private IP ping shows that we have created VPN Tunnel between AWS & Azure.
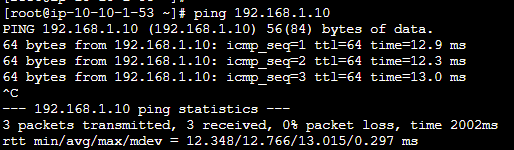
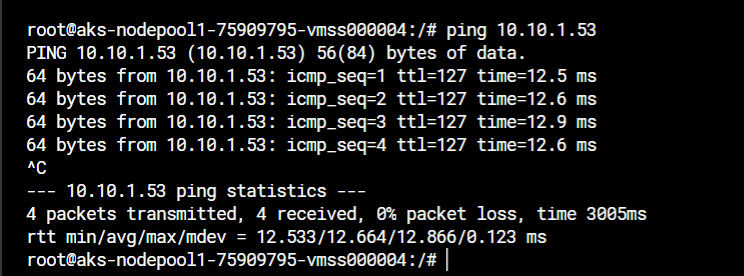

.svg)
%20(2).png)



.png)
